Setting up a Qlik Sense Hybrid Environment
I’ve been working recently on getting our internal Qlik Sense Client-Managed environments migrated to Azure (both for hosting and authentication) as well as working smoothly and securely with Qlik Sense SaaS. There have been a few things learned along the way so I thought I’d share some of them. Please note it’s not a step-by-step guide to creating a Qlik Sense Hybrid Environment – although that may follow in the future.
If you’ve been asking any of these questions then hopefully this will be helpful for you:
- How do I avoid licence allocation duplication between Qlik Sense on-premise and cloud?
- How do I get SHA-256 encryption working with SAML authentication in Qlik Sense on-prem?
- How do I synchronise users from a local domain whilst using SAML SSO?
Note that I don’t cover multi-cloud in this article – hopefully we can do that in the future.
TL;DR;
Here’s a high level view of what we have implemented:
Qlik Sense Client-Managed
- Running on a domain-joined Azure Virtual Machine behind an Azure Application Gateway with WAF enabled
- NTLM authentication only possible from internal network – users synchronised using the default User Directory Connector with the default domain
- SSO via Azure AD using SAML – users synchronised using a Generic LDAP User Directory Connector with a different directory name and using email address as the user ID
Qlik Sense SaaS
- SSO via Azure AD using OpenID Connect with the Realm set to the directory name from the client-managed SSO and the email address as the user ID
Into the Weeds
Some of these components are pretty run of the mill for Qlik Sense deployments with good resources to support implementation but others are a bit more complicated. Let’s take them one at a time.
Running Qlik Sense Client-Managed on Azure
Obviously spinning up a VM in Azure and installing Qlik Sense Enterprise is super simple. However, I wanted it behind an additional layer of security rather than leaving Qlik Sense exposed directly on the internet.
So we set up an Application Gateway with WAF enabled. I enabled the OWASP rule set but had to add exceptions to this as it kept picking up certain valid traffic as SQL injection attacks or similar. However, having the majority of rules enabled gives me some comfort that we’re covering the bases.
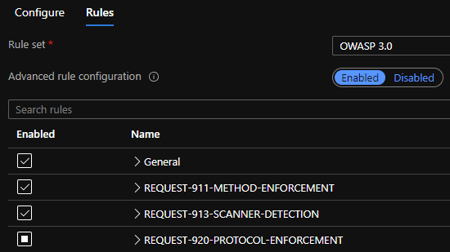
Client-Managed NTLM Authentication
I didn’t change anything here in the end from the base configuration – although I did make sure to only sync existing users since this isn’t going to be used much and I didn’t want all users in my user list (as this would be a duplicate to the other directory).
Potential future improvement – this could be limited to only admins or similar to make sure end users don’t start using this if we wanted to lock things down a bit more.
Client-Managed SSO using Azure AD
The best guide for this is Microsoft’s, but there are some useful additional notes in Qlik’s Knowledgebase article that references that.
The main things I’d note from what I implemented are:
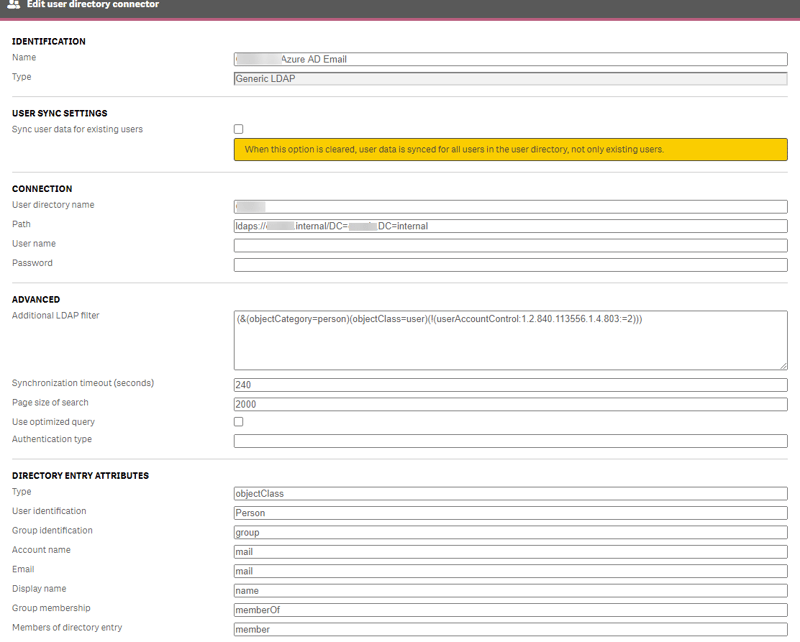
- I used a Generic LDAP User Directory Connector to synchronise users to the Active Directory rather than Azure AD DS since it was on the domain anyway so had access.
- The connection stumped me for a bit but finally using this format in the “Path” worked (obviously domain was replaced with our actual domain):
ldaps://domain.internal/DC=domain,DC=internal - I set Account name to “mail” (not the User identification as I first thought).
- The connection stumped me for a bit but finally using this format in the “Path” worked (obviously domain was replaced with our actual domain):
- I set the unique identifier in the claim mapping in Azure AD to be email address and copied the Claim name (http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress) from Azure into SAML attribute for user directory in Qlik Sense.
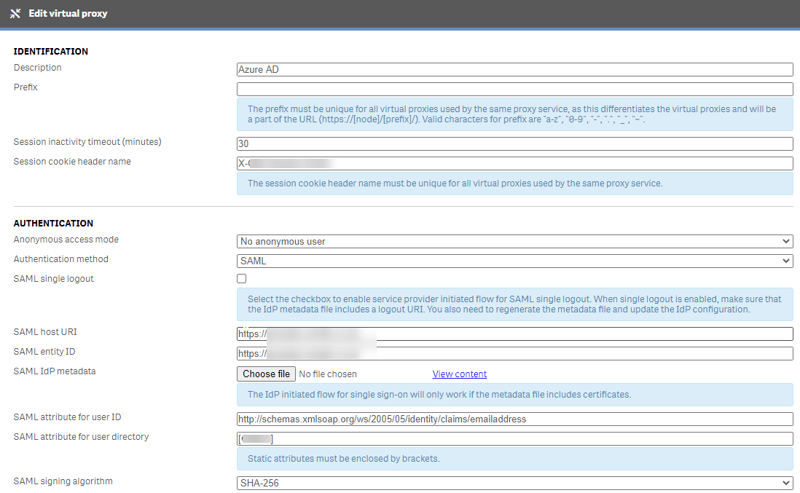
- I had to juggle with SSL certificates to get it to work with SHA-256 – your certificate has to use a specific encryption provider for SAML not just any SHA-256. See this article for how to convert your certs – although we updated our internal Certificate Authority enrolment policy to use this method rather than having to convert them.
SaaS SSO using Azure AD
Whilst it’s not officially supported, and has a few “nuances” when it is used, Azure AD functions just fine as an Identity Provider for Qlik Sense SaaS. Big thanks here goes to Jeff Goldberg who wrote and maintains an article on how to get this working. He also helped me with my setup along with others on the Qlik Branch Slack (a very useful place for such advice). I hope that Qlik soon release further support for Azure AD in there – the main limitation is currently that email addresses come through as unverified although this doesn’t have any immediate impact.
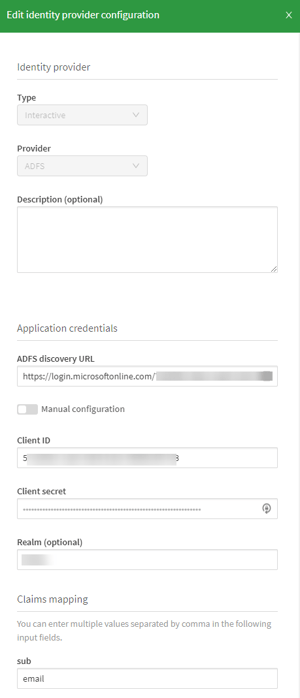
The two things I changed from his setup to make it work with my Client-Managed install were:
- Instead of “sub” I used “mail” in the sub box of the IdP configuration so the email address would be treated as the user ID rather than the random string from Azure AD.
- In Realm I put the Directory that I’d set up for the Generic LDAP User Directory Connector.
- Without this, the email address would come through from SaaS as user.name@domain.com but, from a licence server perspective at least, Client Managed would show this as DIRECTORY\user.name@domain.com so the two would be treated separately.
Qlik Sense Hybrid Environment: Wrapping up
All that was left once that was working was to move users’ content from their “old” user to their “new” one as the email-identified users came through as new ones. Fortunately this was quite a new environment so there wasn’t too much to do.
Qlik Sense Hybrid Environment: What’s next?
You tell me! If you’d like me to go into more detail on one or more section, then please let me know. Next we’ll be setting up multi-cloud app distribution – although with Qlik DataTransfer now around this is slightly less important. Then we’ll be getting NPrinting installed and working through the App Gateway with SAML SSO too. We are aware of a limitation with NPrinting On Demand only working with NTLM so we’ll have to see what workarounds we can find for that, if any. Of course we’ll want Alerting in there too and, eventually some of the QDI products (Replicate / Compose / Catalog) in the back-end. Watch this space…
By Alex Walker





Comments